Finding the best credit card processing company for your business can be an adventure — and not always the best kind. Here are some pitfalls to avoid when performing your search.
Long-Term Contracts and/or Early Termination Fees
Be wary of processors asking you to sign a long-term contract with early termination fees. It’s common in the industry to find contracts of up to five years in length, and some processors have an auto-renewal clause.
In addition, there are processors who don’t charge a flat early termination fee but calculate the amount using a method referred to as “liquidated damages.” With liquidated damages, you’ll be charged the amount in revenue that your processor determines it will lose due to you closing your account. For example, if you have a three-year contract, and you cancel after one year, you will pay a cancellation fee equal to two years worth of processing costs.
Long-Term Non Cancellable Equipment Leases
Leasing versus purchasing a credit card terminal can seem like an affordable option, but lessee beware. Often times, these long-term lease agreements cannot be cancelled, which means that you are the hook for monthly payments for the entire duration of the lease term — even if you switch processors or stop accepting cards altogether .
Unexpected Rate Increases
Don’t fall for the classic “bait and switch.” Processors will quote aritifically low rates only then to raise them a few months later. Always read the Terms and Conditions to ensure that the processing company does not reserve the right to raise your rates.
Confusing Pricing and Statements
Credit card processors employ a few different pricing methods. One in particular — tiered pricing — can lead to confusing, hard-to-understand statements and unexpected higher rates.
With this pricing model, transactions are lumped into “rate buckets,” such as qualified, mid-qualified and non-qualified. Usually the processor advertises the rate associated with the qualified bucket because it is the lowest. What often happens, however, is that a large amount of the merchant’s transactions are downgraded and consequently charged at a higher rate.
Hidden Fees
The devil is in the details. Ask for an outline of all the extra monthly and annual fees you will be charged. Make sure that the rate they quote takes into account all of those fees. Take the time to read through the Terms and Conditions to ensure that what you’re being promised is what you’re going to receive.
In essence, credit card processors are in the “trust” business. You trust them to safely process your credit card receipts for a fair price. By doing some homework, you can help ensure that you find the best processor for your business and its unique needs.





 Posted by POSitive Processing
Posted by POSitive Processing 





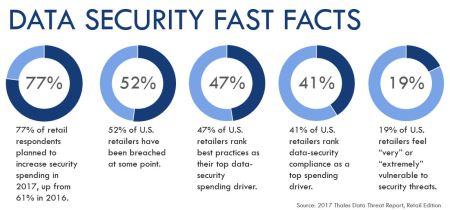 Access the entire report here:
Access the entire report here: